Delay-CJ: A novel cryptojacking covert attack method based on
Por um escritor misterioso
Last updated 17 junho 2024

Cryptojacking is a type of resource embezzlement attack, wherein an attacker secretly executes the cryptocurrency mining program in the target host to…
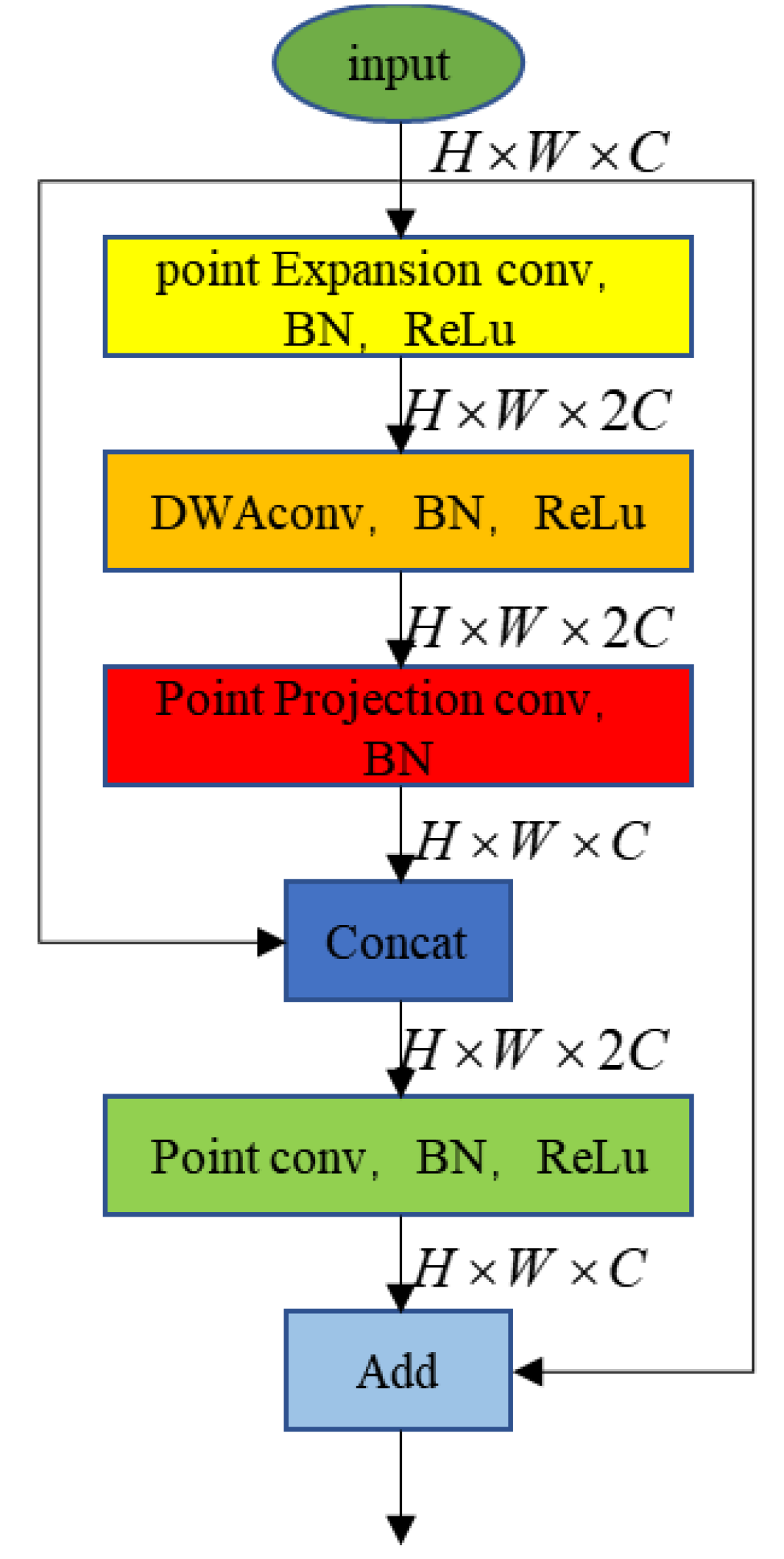
Sensors, Free Full-Text

RAID 2022 – The 25th International Symposium on Research in Attacks, Intrusions and Defenses

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

SHAOYING LIU (Graduate School of Advanced Science and Engineering)

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks
WR.1943-5452.0001265/asset/4d8d4969-3ab3-485d-a969-71e7768e3e7a/assets/images/large/figure2.jpg)
Review of Modeling Methodologies for Managing Water Distribution Security, Journal of Water Resources Planning and Management

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks
Blockchain-Based Data Management System for ETO Manufacturing
CRYINGJACKPOT's general overview

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks
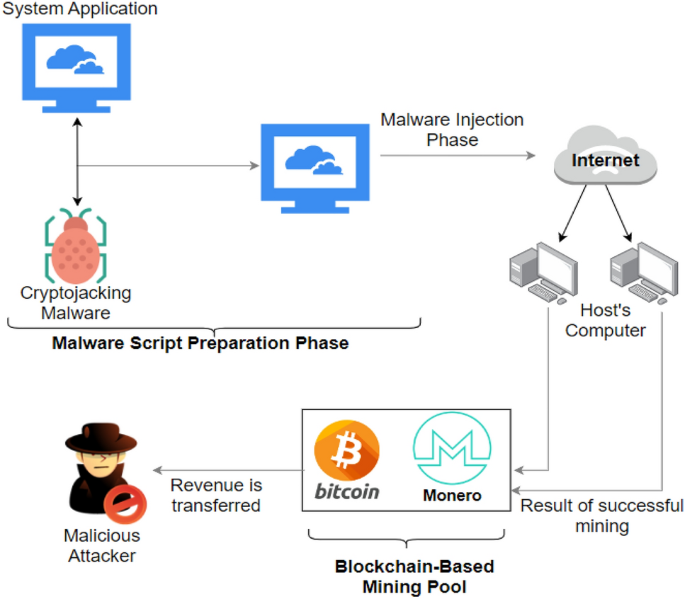
A deep learning approach for host-based cryptojacking malware detection

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks
Recomendado para você
-
minerBlock17 junho 2024
-
 MinerBlock Alternatives and Similar Apps17 junho 2024
MinerBlock Alternatives and Similar Apps17 junho 2024 -
 Anti-Coinminer Mining Campaign17 junho 2024
Anti-Coinminer Mining Campaign17 junho 2024 -
 Fake Ad Blocker Delivers Hybrid Cryptominer/Ransomware Infection17 junho 2024
Fake Ad Blocker Delivers Hybrid Cryptominer/Ransomware Infection17 junho 2024 -
 Opera 50 Beta Version to Come with Cryptocurrency Mining Blocker17 junho 2024
Opera 50 Beta Version to Come with Cryptocurrency Mining Blocker17 junho 2024 -
 Definition of spyware blocker17 junho 2024
Definition of spyware blocker17 junho 2024 -
 AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock17 junho 2024
AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock17 junho 2024 -
 Men's Basketball - UTEP Miners17 junho 2024
Men's Basketball - UTEP Miners17 junho 2024 -
 The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost17 junho 2024
The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost17 junho 2024 -
 Miner Blocker - Block Coin Miners for Google Chrome - Extension Download17 junho 2024
Miner Blocker - Block Coin Miners for Google Chrome - Extension Download17 junho 2024
você pode gostar
-
 Pokémon GO Shiny Shadow Articuno, Moltres, Landorus, Lugia x2 - Mini Account (Read Describe) - PoGoFighter17 junho 2024
Pokémon GO Shiny Shadow Articuno, Moltres, Landorus, Lugia x2 - Mini Account (Read Describe) - PoGoFighter17 junho 2024 -
How to find a blobfish in Stardew Valley - Quora17 junho 2024
-
 How To Make The SMALLEST Possible Avatar In Roblox17 junho 2024
How To Make The SMALLEST Possible Avatar In Roblox17 junho 2024 -
 Estratégias Vitoriosas No Xadrez - Yasser Seirawan - Traça Livraria e Sebo17 junho 2024
Estratégias Vitoriosas No Xadrez - Yasser Seirawan - Traça Livraria e Sebo17 junho 2024 -
 Dominó Multiplayer - Jogo Gratuito Online17 junho 2024
Dominó Multiplayer - Jogo Gratuito Online17 junho 2024 -
 Kaguya-sama Love Is War Season 4 Release Date News & Updates!!17 junho 2024
Kaguya-sama Love Is War Season 4 Release Date News & Updates!!17 junho 2024 -
 Winter Friends in Minecraft Marketplace17 junho 2024
Winter Friends in Minecraft Marketplace17 junho 2024 -
 Em 1990, Pantanal chocou com peão castrado e vilão devorado por piranhas · Notícias da TV17 junho 2024
Em 1990, Pantanal chocou com peão castrado e vilão devorado por piranhas · Notícias da TV17 junho 2024 -
 Heimspiel des TSV 1860 gegen SC Verl: Tickets seit Mittwoch im freien Verkauf17 junho 2024
Heimspiel des TSV 1860 gegen SC Verl: Tickets seit Mittwoch im freien Verkauf17 junho 2024 -
 Análise – Pokémon Ultra Sun/Moon – PróximoNível17 junho 2024
Análise – Pokémon Ultra Sun/Moon – PróximoNível17 junho 2024