Thoughts on the Application of Low-Interactive Honeypot Based on Raspberry Pi in Public Security Actual Combat, LIHRP
Por um escritor misterioso
Last updated 27 maio 2024

Full Overview about all of Deutsche Telekom's Honeypot Projects

Create an Army of Raspberry Pi Honeypots on a Budget

HoneyPi - An easy honeypot for a Raspberry Pi - TrustFoundry
Thoughts on the Application of Low-Interactive Honeypot Based on Raspberry Pi in Public Security Actual Combat, LIHRP
Step by Step Guide on setting up SMB, RDP, SSH and HTTP HoneyPot in Raspberry Pi, by Elaine Hung

Thoughts on the Application of Low-Interactive Honeypot Based on Raspberry Pi in Public Security Actual Combat, LIHRP

PART 1: LET'S CREATE A HONEYPOT FROM SCRATCH USING A #RASPBERRYPI #LIVEHACKING #LEARNTOLEARN

Enhancing Cybersecurity with Low-Interaction Honeypots: A Strategic Approach to Threat Intelligence

Turn a Raspberry Pi into a network honeypot : r/raspberry_pi
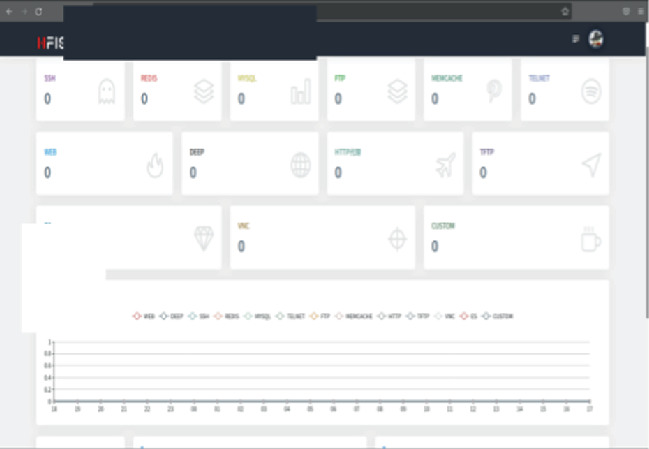
Thoughts on the Application of Low-Interactive Honeypot Based on Raspberry Pi in Public Security Actual Combat, LIHRP

Honeypots for Employee Information Security Awareness and Education Training: A Conceptual EASY Training Model - ScienceDirect

Create a Security Honey Pot with OpenCanary and a Raspberry Pi 3 (Updated 2021) - Bob McKay's Blog

Honeypots: Tracking Hackers, Guide books

PDF) A new dynamic security defense system based on TCP_REPAIR and deep learning
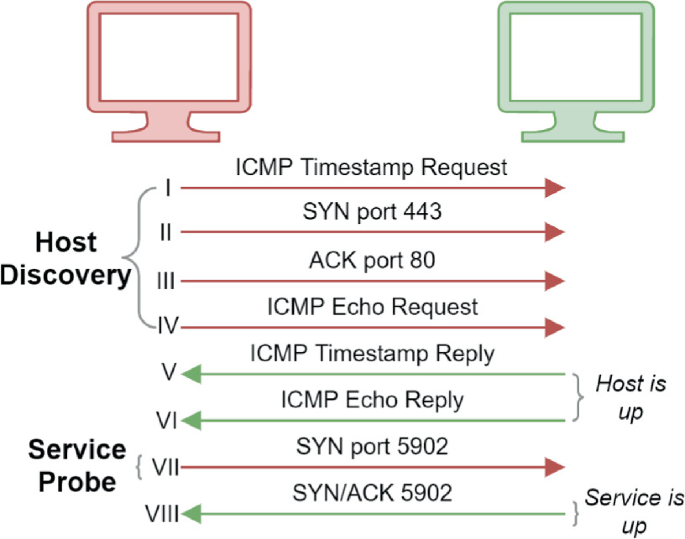
Lightweight On-Demand Honeypot Deployment for Cyber Deception
Recomendado para você
-
IP Grabber - Microsoft Apps27 maio 2024
-
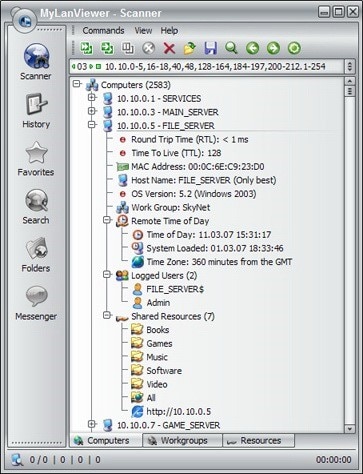 The 7 Best IP Address Trackers - DNSstuff27 maio 2024
The 7 Best IP Address Trackers - DNSstuff27 maio 2024 -
how to create a ip grabber|TikTok Search27 maio 2024
-
discord-token-grabber · GitHub Topics · GitHub27 maio 2024
-
Is an IP Grabber? - Quora27 maio 2024
-
 How to Find the IP Address of a Skype User (with Pictures)27 maio 2024
How to Find the IP Address of a Skype User (with Pictures)27 maio 2024 -
 13+ Best Web Scraping Tools to Unlock the Hidden27 maio 2024
13+ Best Web Scraping Tools to Unlock the Hidden27 maio 2024 -
National Cyber Security Services - Ghost Eye - #Information #Gathering #Tool #Ghost Eye is an Information Gathering Tool made in #python 3. To run Ghost Eye, it only needs a #domain or #27 maio 2024
-
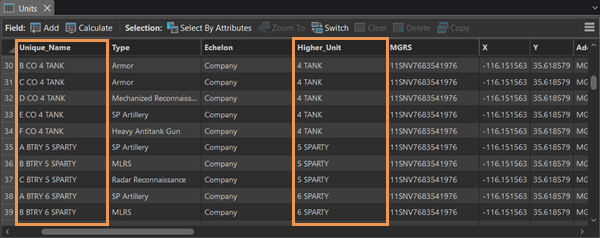 Link charts in ArcGIS AllSource, Part 1: Create your first link chart27 maio 2024
Link charts in ArcGIS AllSource, Part 1: Create your first link chart27 maio 2024 -
![Discord IP Resolver How to Pull IP on Discord? [2023 Update] - MiniTool Partition Wizard](https://www.partitionwizard.com/images/uploads/articles/2022/08/discord-ip-resolver/discord-ip-resolver-5.png) Discord IP Resolver How to Pull IP on Discord? [2023 Update] - MiniTool Partition Wizard27 maio 2024
Discord IP Resolver How to Pull IP on Discord? [2023 Update] - MiniTool Partition Wizard27 maio 2024
você pode gostar
-
 Why Pyramid Head is the most disturbing video game character ever27 maio 2024
Why Pyramid Head is the most disturbing video game character ever27 maio 2024 -
 Convite Animado (VÍDEO) para Aniversário do NARUTO27 maio 2024
Convite Animado (VÍDEO) para Aniversário do NARUTO27 maio 2024 -
 Pokemon Crystal ONIX Minecraft Map27 maio 2024
Pokemon Crystal ONIX Minecraft Map27 maio 2024 -
.png) Trade Roblox Anime Adventures Items27 maio 2024
Trade Roblox Anime Adventures Items27 maio 2024 -
Buy Saints Row The Third Remastered27 maio 2024
-
DLC PES 2011 1.0 Download (Free)27 maio 2024
-
 New world champ Ding Liren returns to Hangzhou_The 19th Asian Games Hangzhou27 maio 2024
New world champ Ding Liren returns to Hangzhou_The 19th Asian Games Hangzhou27 maio 2024 -
Alien x vs cosmic garou27 maio 2024
-
 ENCHEI-VOS DO ESPÍRITO SANTO27 maio 2024
ENCHEI-VOS DO ESPÍRITO SANTO27 maio 2024 -
 Emotions Blue Eyes Of Anime Manga Girls Stock Illustration27 maio 2024
Emotions Blue Eyes Of Anime Manga Girls Stock Illustration27 maio 2024