Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 09 junho 2024
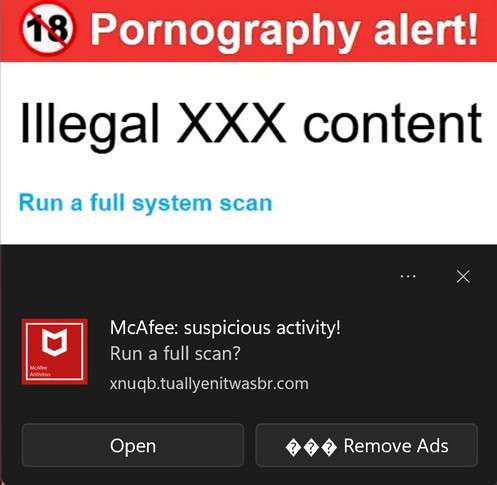
Remove McAfee Suspicious Activity Pop-ups [Virus Removal]
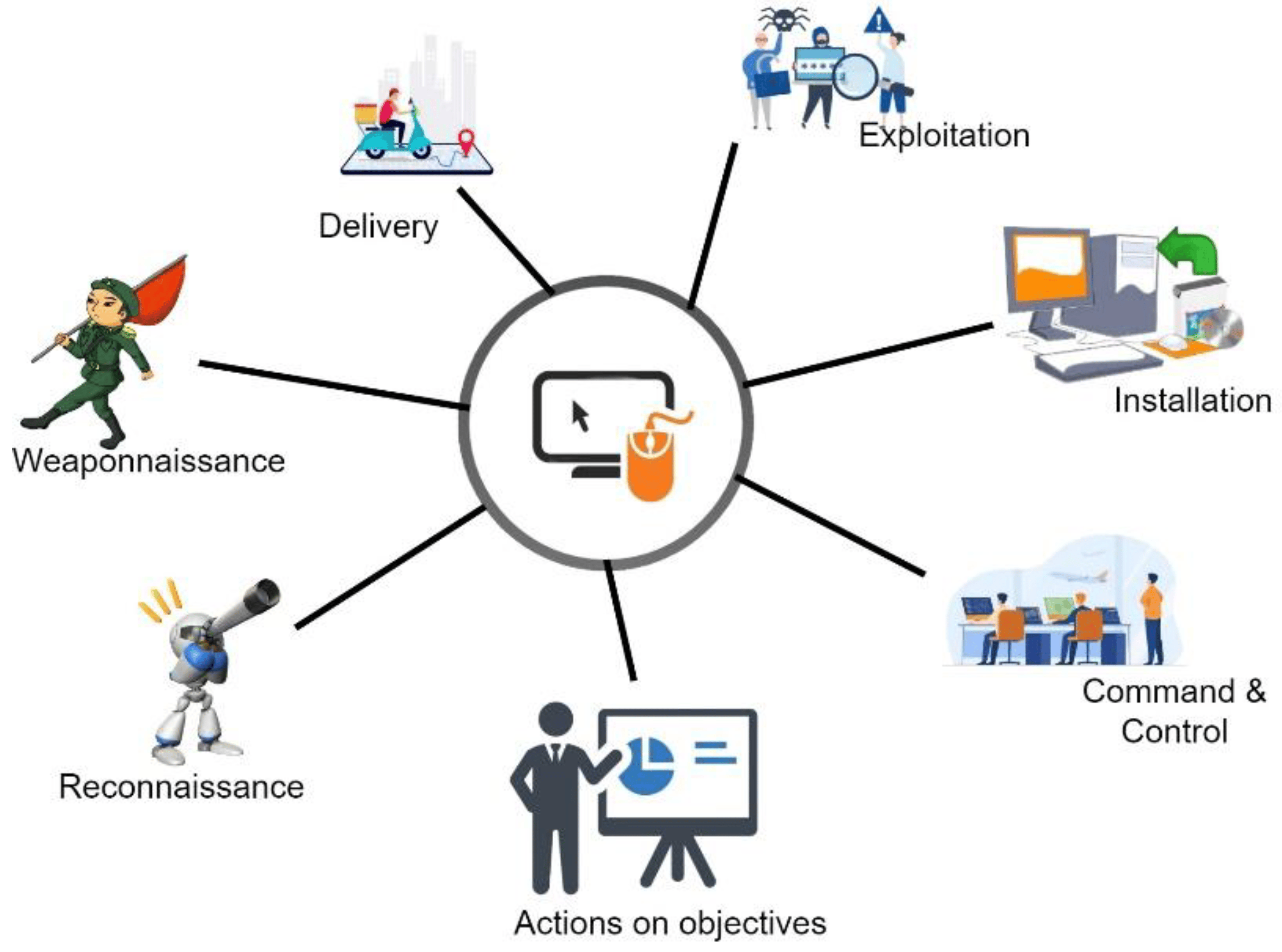
Symmetry, Free Full-Text
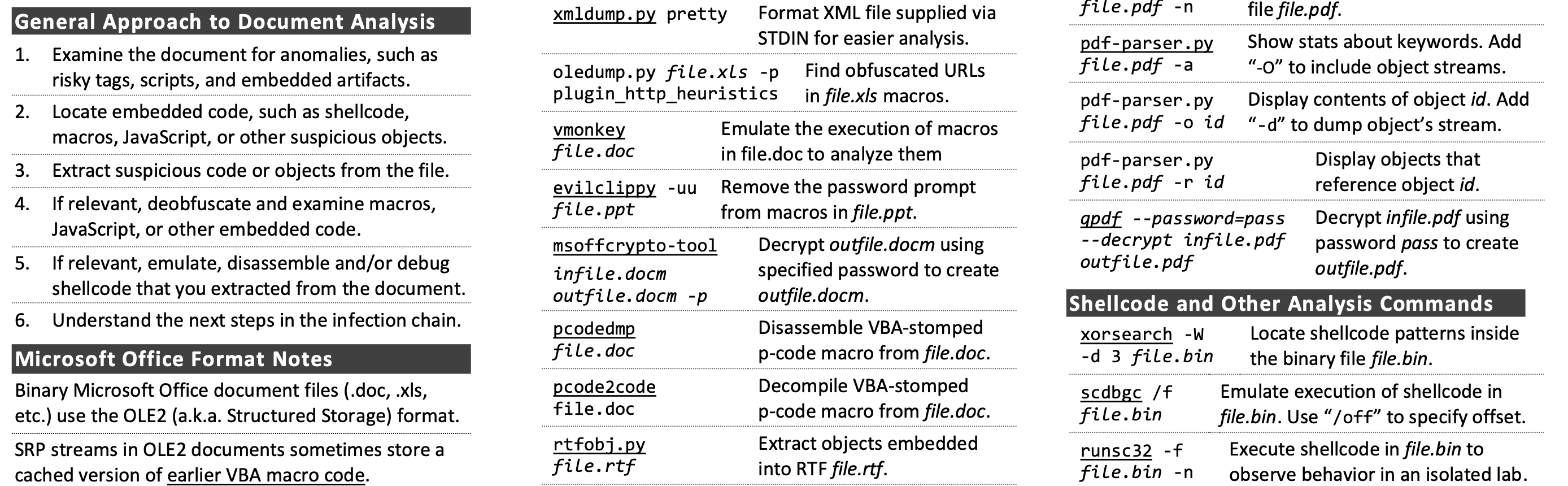
Analyzing Malicious Documents Cheat Sheet

US Cyber Command, DHS-CISA release Russian malware samples tied to

The Top 10 Malware Analysis Tools
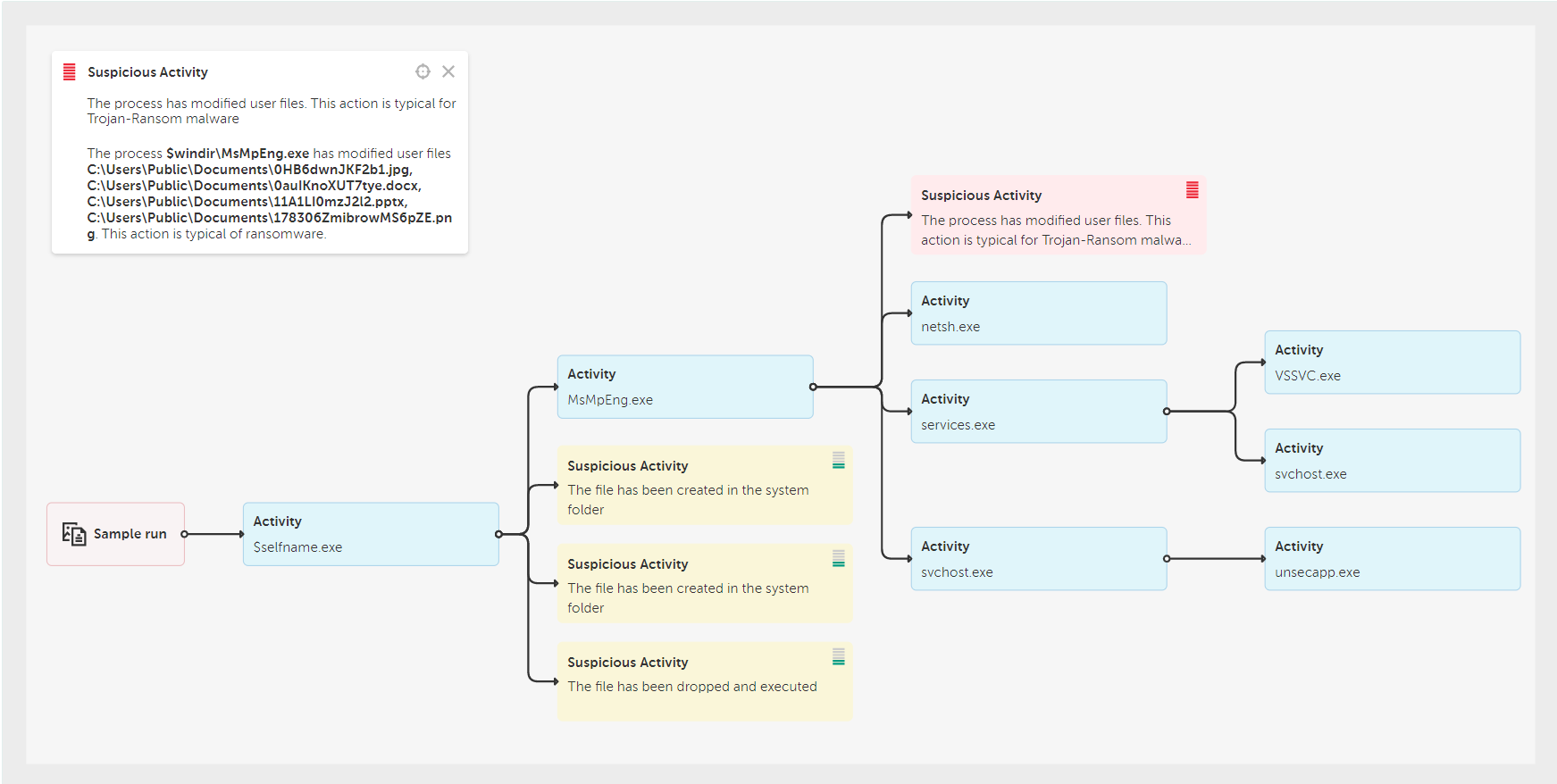
REvil ransomware attack against MSPs and its clients around the
A Basic Malware Analysis Walkthrough, by Dan Crossley
What is Malware Analysis? - SOC Prime
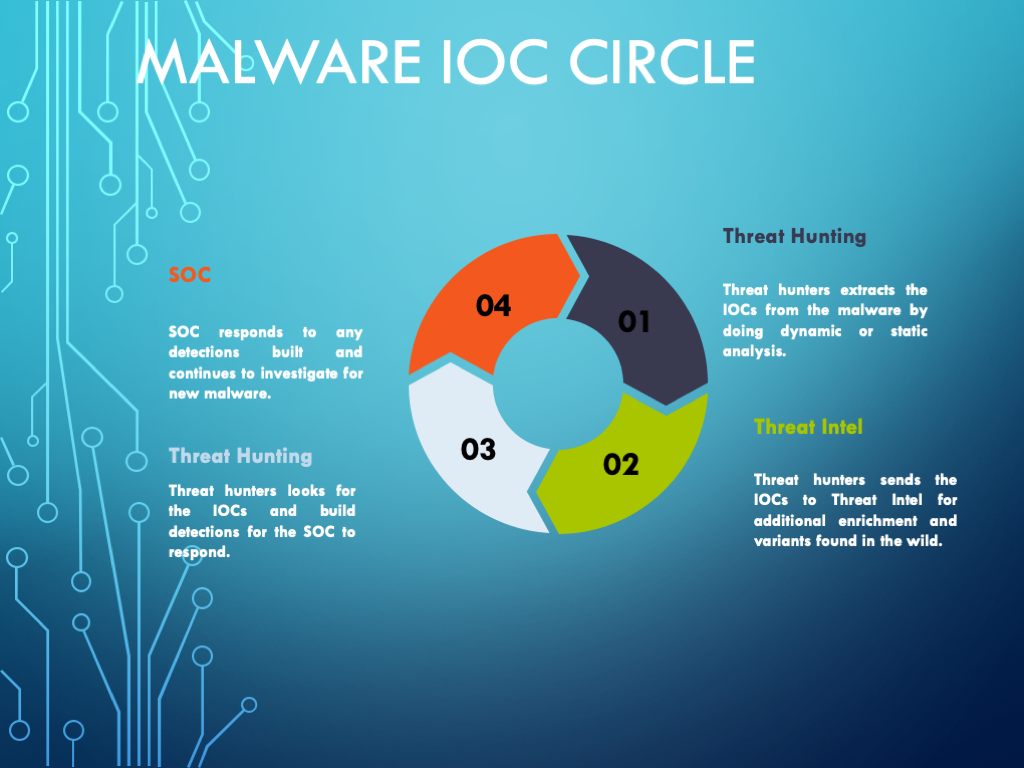
Malware Analysis Framework v1.0

Dismantling ZLoader: How malicious ads led to disabled security

Using Python for Malware Analysis — A Beginners Guide

Why Do You Need a Malware Sandbox? - Cyber Defense Magazine

Remediation and Malware Detection Overview

Election Security Spotlight – Malware Analysis
Recomendado para você
-
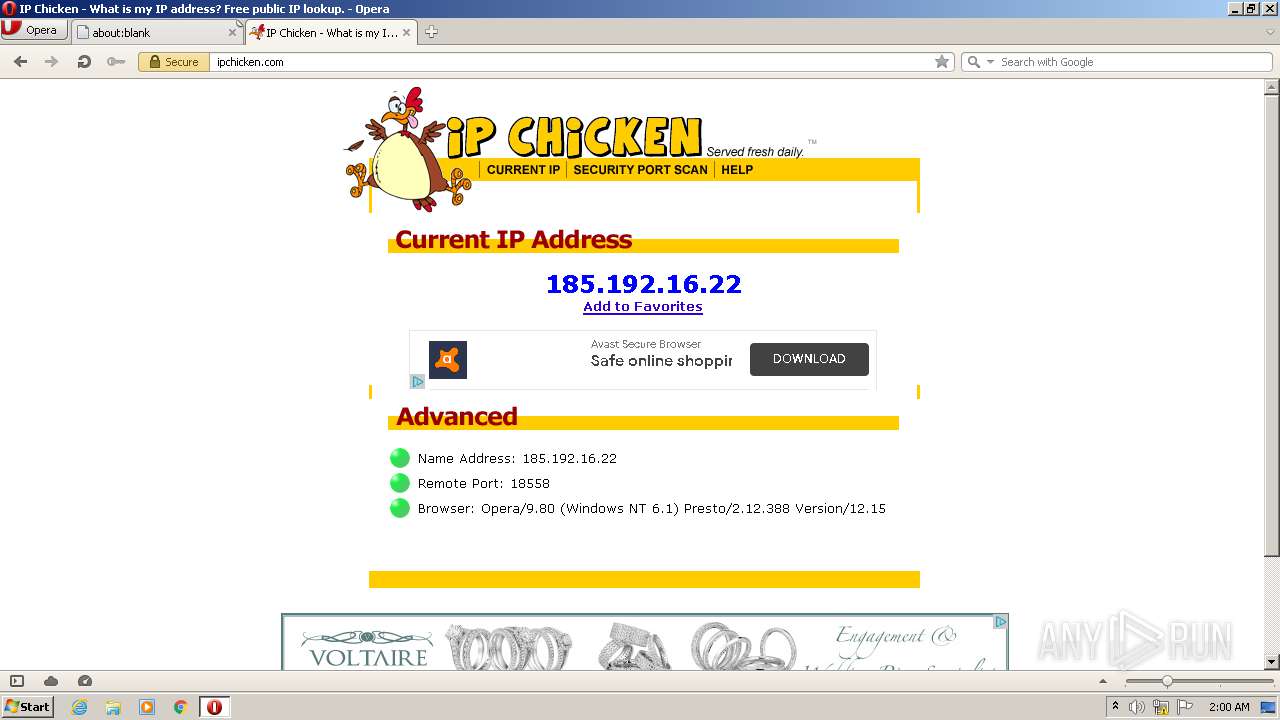
 How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey09 junho 2024
How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey09 junho 2024 -
 IPChicken, Woo hoo! Lightspeed!, Richard De Guzman09 junho 2024
IPChicken, Woo hoo! Lightspeed!, Richard De Guzman09 junho 2024 -
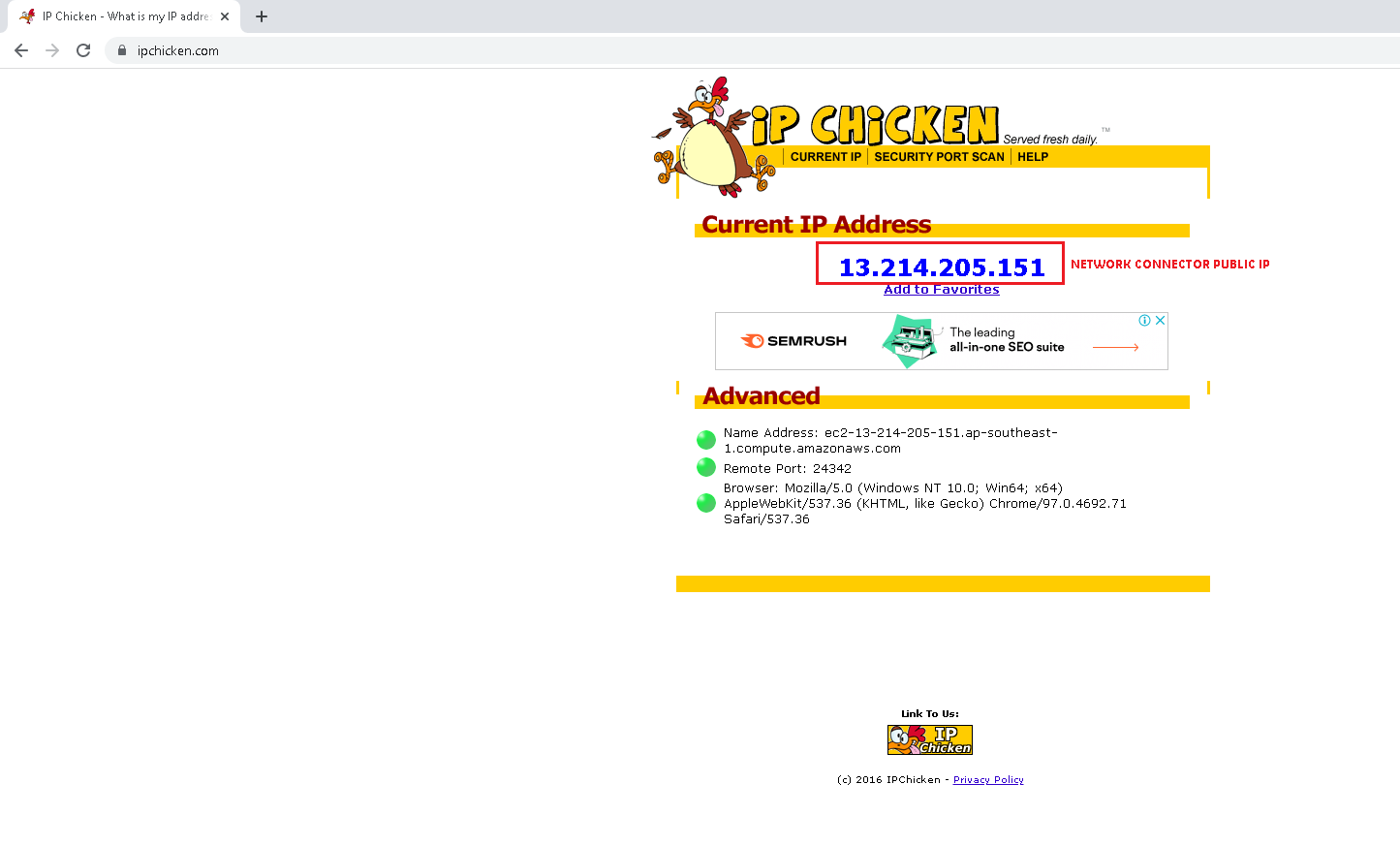 CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center09 junho 2024
CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center09 junho 2024 -
 like ip chicken 🐔🐔🐔 Ip chicken, Smart city, Coding09 junho 2024
like ip chicken 🐔🐔🐔 Ip chicken, Smart city, Coding09 junho 2024 -
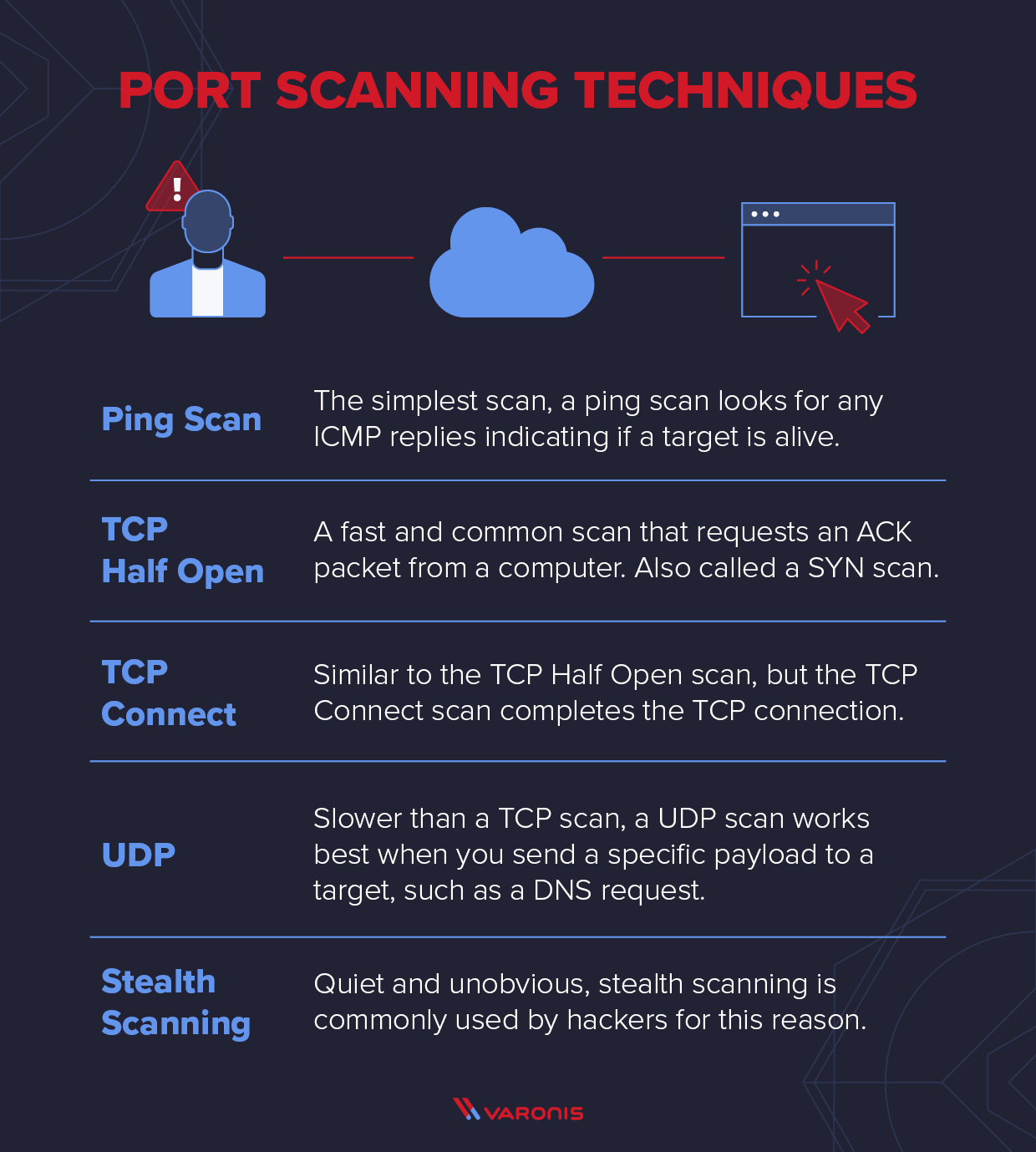 Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi09 junho 2024
Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi09 junho 2024 -
 Brisson teaches internet safety - Munising Beacon09 junho 2024
Brisson teaches internet safety - Munising Beacon09 junho 2024 -
 What is a Port Scanner and How Does it Work?09 junho 2024
What is a Port Scanner and How Does it Work?09 junho 2024 -
 Malware analysis Malicious activity09 junho 2024
Malware analysis Malicious activity09 junho 2024 -
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager09 junho 2024
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager09 junho 2024 -
 Install Tor on Ubuntu 18.04 Bionic Beaver Linux - Linux Tutorials - Learn Linux Configuration09 junho 2024
Install Tor on Ubuntu 18.04 Bionic Beaver Linux - Linux Tutorials - Learn Linux Configuration09 junho 2024
você pode gostar
-
![Coatless Bridget [GUILTY GEAR -STRIVE-] [Mods]](https://images.gamebanana.com/img/ss/mods/530-90_62f34841c8fcd.jpg) Coatless Bridget [GUILTY GEAR -STRIVE-] [Mods]09 junho 2024
Coatless Bridget [GUILTY GEAR -STRIVE-] [Mods]09 junho 2024 -
 Hunter x Hunter- Leorio Enamel Pin – magicalmaidens09 junho 2024
Hunter x Hunter- Leorio Enamel Pin – magicalmaidens09 junho 2024 -
 Team Hot Wheels Rubble Ruckus : Blit Interactive : Free Download, Borrow, and Streaming : Internet Archive09 junho 2024
Team Hot Wheels Rubble Ruckus : Blit Interactive : Free Download, Borrow, and Streaming : Internet Archive09 junho 2024 -
 Cambridge Utd FC x Tottenham Hotspur Sub21 » Placar ao vivo09 junho 2024
Cambridge Utd FC x Tottenham Hotspur Sub21 » Placar ao vivo09 junho 2024 -
 Lords of the Fallen Previews09 junho 2024
Lords of the Fallen Previews09 junho 2024 -
 LEGO Sonic the Hedgehog Sonic vs. Dr. Eggman's Death Egg Robot Toy09 junho 2024
LEGO Sonic the Hedgehog Sonic vs. Dr. Eggman's Death Egg Robot Toy09 junho 2024 -
 SCP-3812, All Fiction Battles Wiki09 junho 2024
SCP-3812, All Fiction Battles Wiki09 junho 2024 -
 Tartarugas Ninja” fascina na animação e brilha nos heróis • DOL09 junho 2024
Tartarugas Ninja” fascina na animação e brilha nos heróis • DOL09 junho 2024 -
Mama Money - Mama's Family App now available for download from09 junho 2024
-
 Yu-Gi-Oh 5D's World Championship 2011 Over the Nexus (DS) CIB w/ Promo Cards 8371724182909 junho 2024
Yu-Gi-Oh 5D's World Championship 2011 Over the Nexus (DS) CIB w/ Promo Cards 8371724182909 junho 2024
