Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 17 junho 2024

Malware Analysis and Reverse Engineering, by Ensar Seker

10 Best Malware Analysis Tools - Updated 2023! (Paid & Free)

Malware Detection & Top Techniques Today
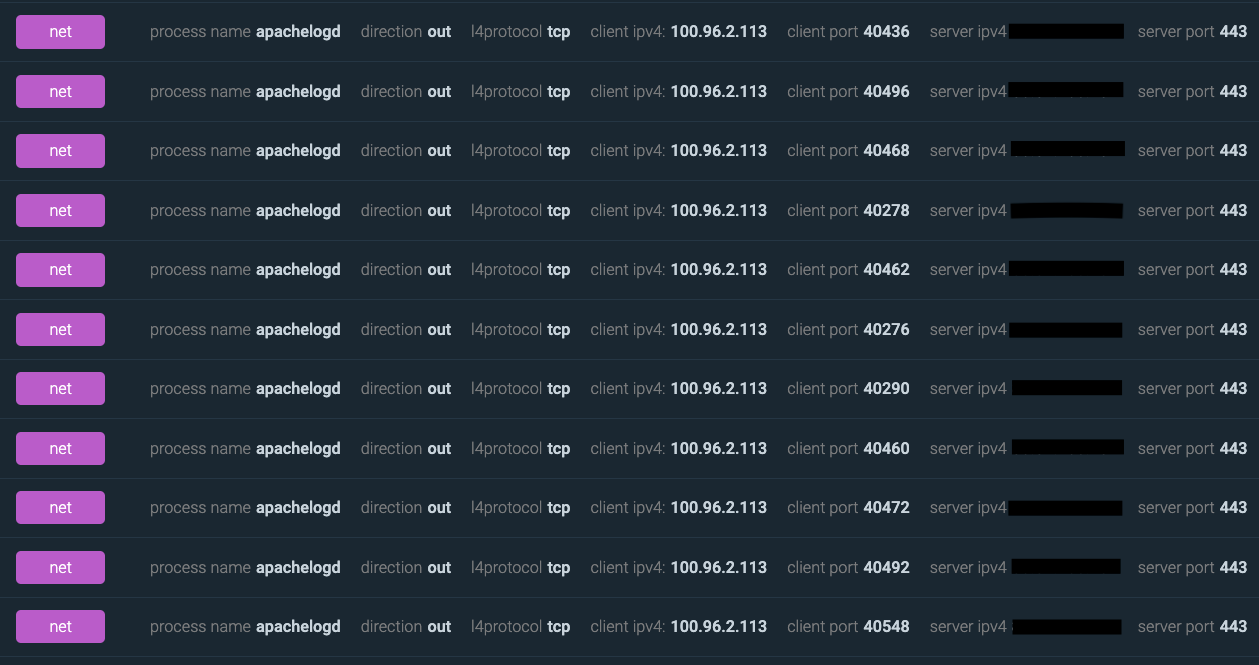
Malware analysis: Hands-On Shellbot malware – Sysdig
How to Detect Running Malware - Intro to Incident Response Triage 2021
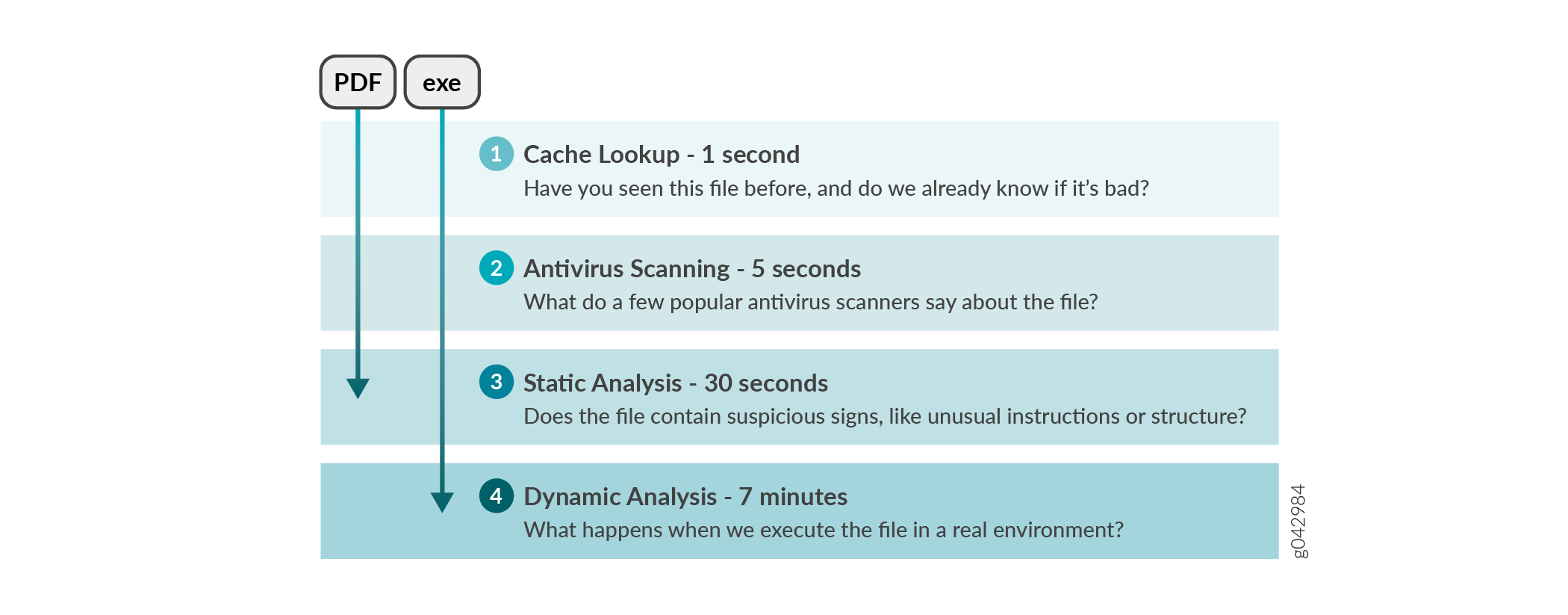
How is Malware Analyzed and Detected?, ATP Cloud

Dismantling ZLoader: How malicious ads led to disabled security
How to Get Free Malware Samples and Reports - 's
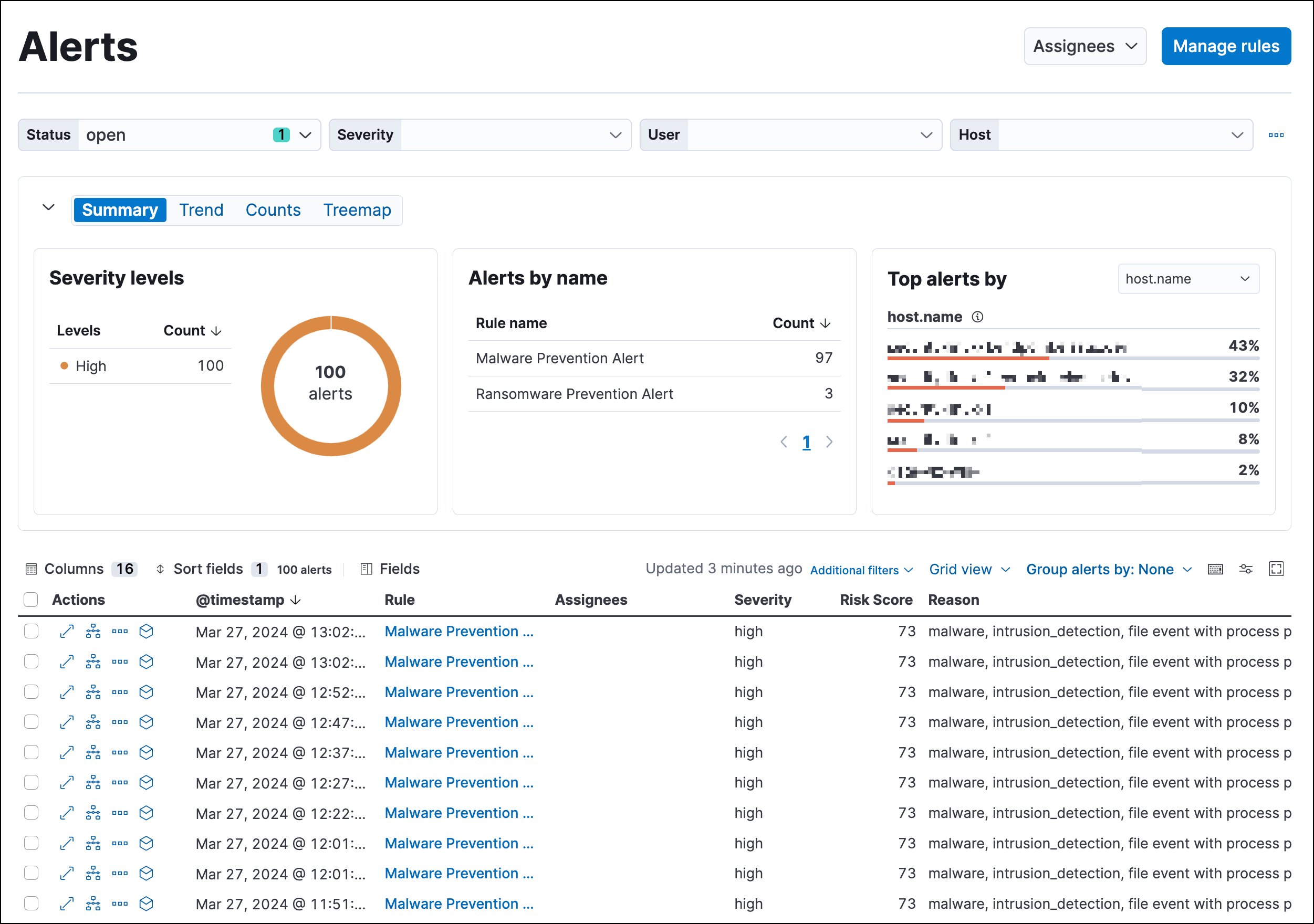
Detections and alerts, Elastic Security Solution [8.11]

Malware Detection: 7 Methods and Security Solutions that Use Them

How Malware Analysis Works - NetWitness Community - 669511

Unusual Activity Detection – Identifying and Flagging Security

Security Orchestration Use Case: Automating Malware Analysis
Recomendado para você
-
Hacking Simulator! - Roblox17 junho 2024
-
 Roblox Mod Apk 2.605.660 (Mega Mod Menu, Unlimited Robux)17 junho 2024
Roblox Mod Apk 2.605.660 (Mega Mod Menu, Unlimited Robux)17 junho 2024 -
 Cuidado! Extensão do Chrome rouba dados de conta no Roblox17 junho 2024
Cuidado! Extensão do Chrome rouba dados de conta no Roblox17 junho 2024 -
FREE ADMIN] - Roblox17 junho 2024
-
 Roblox Hack EXCLUSIVE Download17 junho 2024
Roblox Hack EXCLUSIVE Download17 junho 2024 -
 this is the new roblox hacker. if you play roblox plz stay safe. I am trying to help. on jun1st she will hack ragdoll if you see her. exit out of game17 junho 2024
this is the new roblox hacker. if you play roblox plz stay safe. I am trying to help. on jun1st she will hack ragdoll if you see her. exit out of game17 junho 2024 -
Roblox Cursors HD17 junho 2024
-
:strip_icc()/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/L/9/A1pz9qTqWPixxA1dhC4Q/53586714-10156765096323580-9108199108673273856-n.jpg) Roblox permite hacks? Veja práticas proibidas na plataformas de games17 junho 2024
Roblox permite hacks? Veja práticas proibidas na plataformas de games17 junho 2024 -
Roblox Mod Apk Unlimited Robux 2022 For Android17 junho 2024
-
 Electron x New Executor Free, Roblox x Best Electron Script17 junho 2024
Electron x New Executor Free, Roblox x Best Electron Script17 junho 2024
você pode gostar
-
ROBLOX Roblox Tienda Avatar - Punk s Not Dead17 junho 2024
-
 Vegan Drag Queen Scaredy Kat To Compete In Ru Paul's UK Show17 junho 2024
Vegan Drag Queen Scaredy Kat To Compete In Ru Paul's UK Show17 junho 2024 -
 The Game Awards 2019: All Major Announcements, Including Senua's Saga: Hellblade II, Godfall17 junho 2024
The Game Awards 2019: All Major Announcements, Including Senua's Saga: Hellblade II, Godfall17 junho 2024 -
 Best Soccer Games On Roblox17 junho 2024
Best Soccer Games On Roblox17 junho 2024 -
 Laptop Pack 217 junho 2024
Laptop Pack 217 junho 2024 -
 Autopecas Rei dos Reis 32303722000101 Carpina17 junho 2024
Autopecas Rei dos Reis 32303722000101 Carpina17 junho 2024 -
Grand Jail Prison Break Escape - Apps on Google Play17 junho 2024
-
 Roblox - DESAFIO NÃO PODE FALAR O NOME JOGANDO PIGGY (Piggy Roblox)17 junho 2024
Roblox - DESAFIO NÃO PODE FALAR O NOME JOGANDO PIGGY (Piggy Roblox)17 junho 2024 -
 Jogo Shadow of the Tomb Raider - PS4 - Limmax17 junho 2024
Jogo Shadow of the Tomb Raider - PS4 - Limmax17 junho 2024 -
 My dog stepped on a bee (Tiktok chain) #amberheard17 junho 2024
My dog stepped on a bee (Tiktok chain) #amberheard17 junho 2024
![FREE ADMIN] - Roblox](https://tr.rbxcdn.com/72fb2913d0ce11c89858adb553a37e80/500/280/Image/Jpeg)

