How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 17 junho 2024
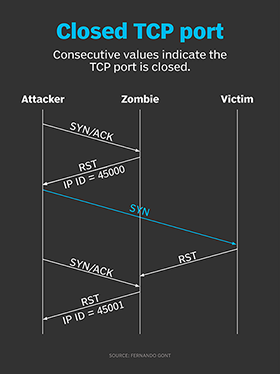
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
What Is Nmap? A Comprehensive Tutorial For Network Mapping

How hackers use idle scans in port scan attacks

How hackers use idle scans in port scan attacks

Port Scan Attack】Definition, Examples, and Prevention
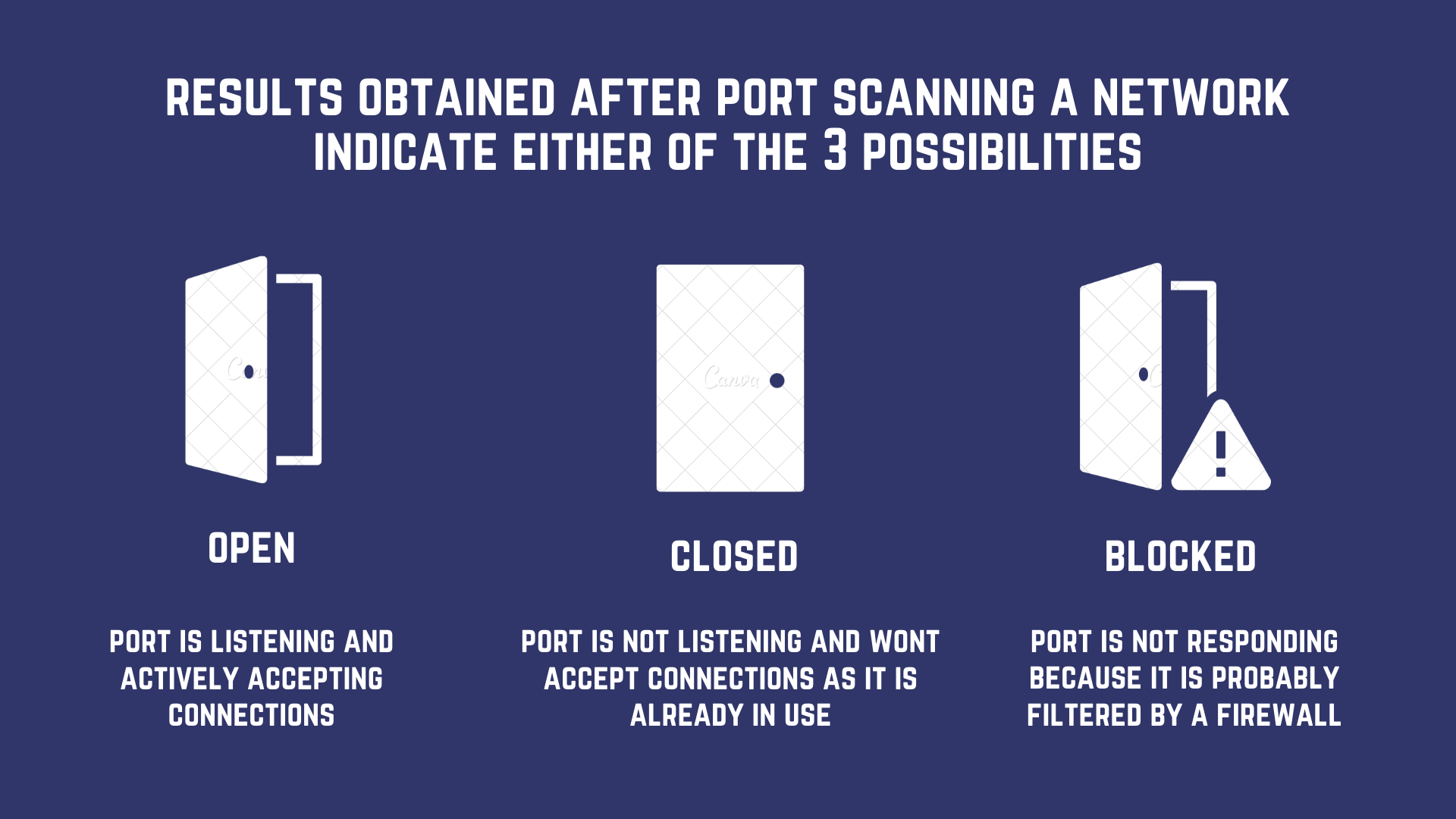
Port Scanning based Attacks

Port Scanning - an overview
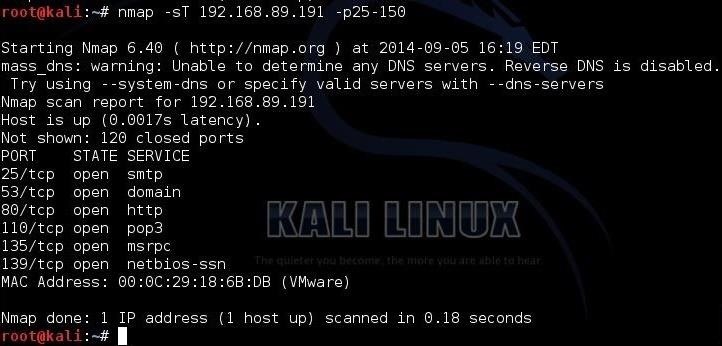
Hack Like a Pro: Advanced Nmap for Reconnaissance « Null Byte :: WonderHowTo

PDF) Surveying Port Scans and Their Detection Methodologies

What is a Port Scanner and How Does it Work?
What Is Nmap? A Comprehensive Tutorial For Network Mapping

How to hide yourself using Idle scan (-sl) - Port scanning tutorial
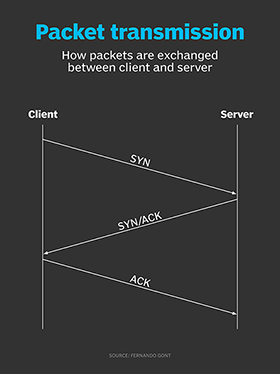
How hackers use idle scans in port scan attacks

Port Scanning: A Comprehensive Guide for Safeguarding Cyberspace
Recomendado para você
-
 What does your IP address say about you? - CNET17 junho 2024
What does your IP address say about you? - CNET17 junho 2024 -
After exchanging my SWITCH to a ROUTER, I… - Apple Community17 junho 2024
-
 IP Chicken - Served Fresh Daily17 junho 2024
IP Chicken - Served Fresh Daily17 junho 2024 -
 HY-VPN – Checking functionality and errors (Linux)17 junho 2024
HY-VPN – Checking functionality and errors (Linux)17 junho 2024 -
![Question] How to get around VPN blockers?](https://i.gyazo.com/f0c5d0d5b114f0d49954a16dd5112ac7.png) Question] How to get around VPN blockers?17 junho 2024
Question] How to get around VPN blockers?17 junho 2024 -
 Install Tor proxy on Ubuntu 22.04 Linux - Linux Tutorials - Learn Linux Configuration17 junho 2024
Install Tor proxy on Ubuntu 22.04 Linux - Linux Tutorials - Learn Linux Configuration17 junho 2024 -
 nexuscyberinfo17 junho 2024
nexuscyberinfo17 junho 2024 -
 Malware analysis Malicious activity17 junho 2024
Malware analysis Malicious activity17 junho 2024 -
 Alt using troll awareness meme - Imgflip17 junho 2024
Alt using troll awareness meme - Imgflip17 junho 2024 -
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager17 junho 2024
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager17 junho 2024
você pode gostar
-
 24 of the Most Powerful Life Lessons17 junho 2024
24 of the Most Powerful Life Lessons17 junho 2024 -
hitman style hajime no ippo|Pesquisa do TikTok17 junho 2024
-
 xeque-mate Tradução de xeque-mate no Dicionário Infopédia de Português - Inglês17 junho 2024
xeque-mate Tradução de xeque-mate no Dicionário Infopédia de Português - Inglês17 junho 2024 -
 Gargoyle - Character (104143) - AniDB17 junho 2024
Gargoyle - Character (104143) - AniDB17 junho 2024 -
![OC] Sorry for this. “Shin Kingpin” : r/Spiderman](https://i.redd.it/6q5wrty0s84b1.jpg) OC] Sorry for this. “Shin Kingpin” : r/Spiderman17 junho 2024
OC] Sorry for this. “Shin Kingpin” : r/Spiderman17 junho 2024 -
 Xbox Game Pass revela jogos que chegam em novembro17 junho 2024
Xbox Game Pass revela jogos que chegam em novembro17 junho 2024 -
 REVERSE CARD SURREM I I I I Esse Reverse Card se encontra no seu estado supremo, ele é capaz de reverter tudo nada é capaz de anular seu efeito CARD MAKER FOR - iFunny Brazil17 junho 2024
REVERSE CARD SURREM I I I I Esse Reverse Card se encontra no seu estado supremo, ele é capaz de reverter tudo nada é capaz de anular seu efeito CARD MAKER FOR - iFunny Brazil17 junho 2024 -
 Battle for Earth - Conflict - Halopedia, the Halo wiki17 junho 2024
Battle for Earth - Conflict - Halopedia, the Halo wiki17 junho 2024 -
 Legend of Zelda Craft Minecraft Texture Packs17 junho 2024
Legend of Zelda Craft Minecraft Texture Packs17 junho 2024 -
Baixar jogo de tiro de matar zumbi para PC - LDPlayer17 junho 2024
