Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 20 junho 2024

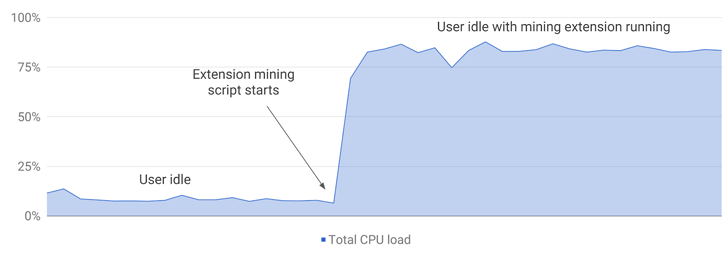
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

Security Delta (HSD) Trend snippet: 2021 Trends in Cryptojacking

ETL2020-Cryptojacking e BOOK EN- Enisa Amenaza #15 - From January

30 Docker images downloaded 20M times in cryptojacking attacks

The concept of cryptojacking and how it works?

How Hackers Use Cryptojacking Malware to Take Over Computers to
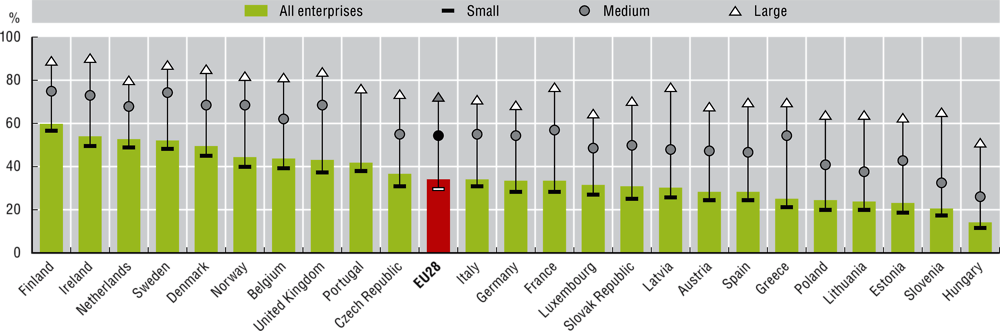
Chapter 7. Digital security OECD Digital Economy Outlook 2020

Awareness Articles – TPS ASAG – Application Security Awareness Group

Defeat Crypto jacking with Decryption and Inspection IT Voice

ENISA Threat Landscape 2022, PDF, Malware
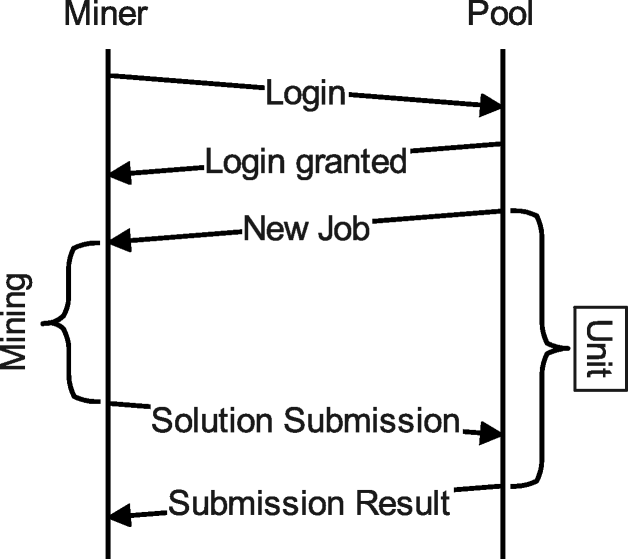
Detection of illicit cryptomining using network metadata

Defeat Cryptojacking with Decryption and Inspection

Defeat Cryptojacking with Decryption and Inspection
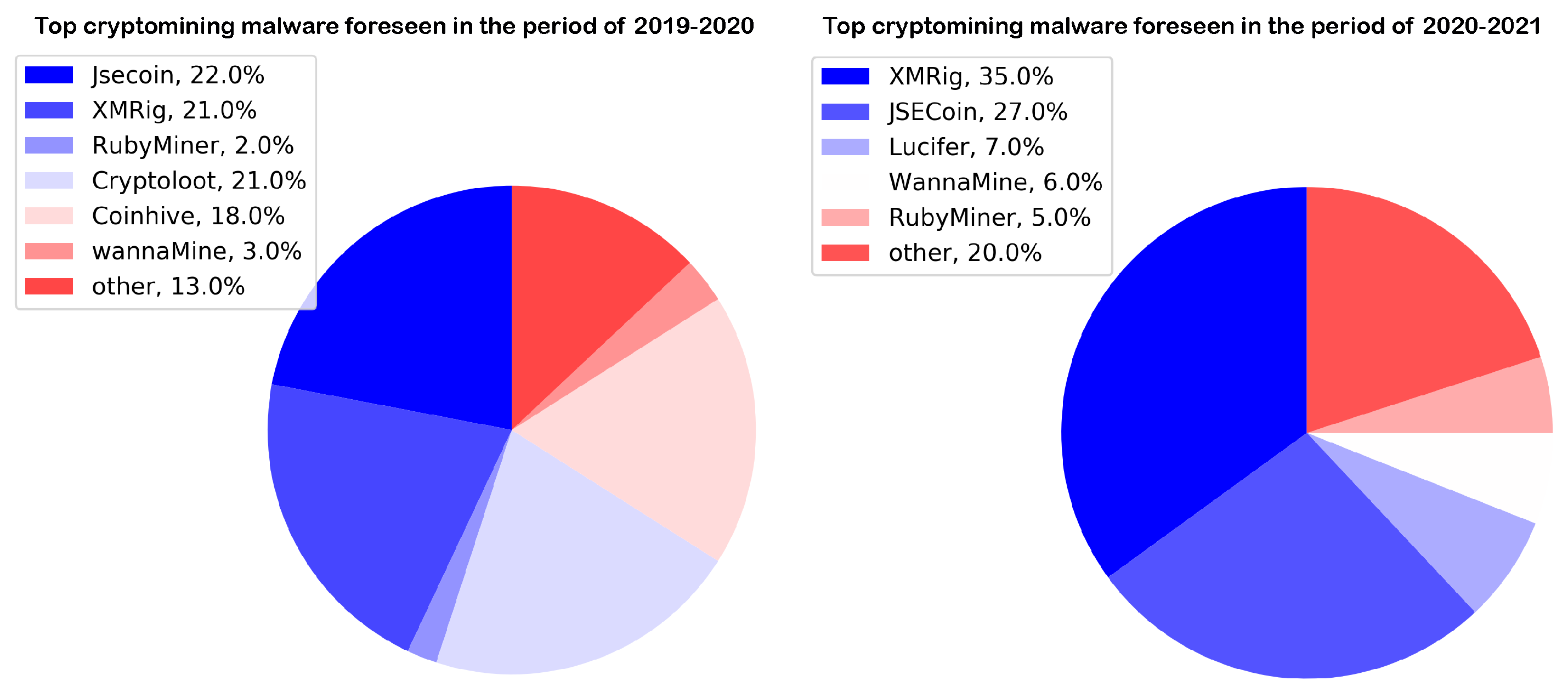
Applied Sciences, Free Full-Text

What is cryptojacking and how can you be affected? - alfa.cash blog

Cryptojacking - Cryptomining in the browser — ENISA
Recomendado para você
-
 Google Bans Cryptocurrency Mining Extensions From Chrome Web Store20 junho 2024
Google Bans Cryptocurrency Mining Extensions From Chrome Web Store20 junho 2024 -
AdBlock for Chrome: How to Block Ads in Chrome, by AdBlock20 junho 2024
-
 Task Mining Desktop Application browser extensions (optional)20 junho 2024
Task Mining Desktop Application browser extensions (optional)20 junho 2024 -
 Blockchain App: First Crypto-Mining Browser Development - Velvetech20 junho 2024
Blockchain App: First Crypto-Mining Browser Development - Velvetech20 junho 2024 -
![5 Best Google Chrome Adblock extensions [Free]](https://cdn.proprivacy.com/storage/images/proprivacy/2022/03/adblock-plusjpg-content_image-default.png) 5 Best Google Chrome Adblock extensions [Free]20 junho 2024
5 Best Google Chrome Adblock extensions [Free]20 junho 2024 -
 21 Must-Have SEO Chrome Extensions to Follow in 202320 junho 2024
21 Must-Have SEO Chrome Extensions to Follow in 202320 junho 2024 -
Ad Blocker Extensions for Chrome in 202320 junho 2024
-
 How to stop websites from using your computer to mine Bitcoin (and more) - CNET20 junho 2024
How to stop websites from using your computer to mine Bitcoin (and more) - CNET20 junho 2024 -
 Cryptocurrency mining affects over 500 million people. And they have no idea it is happening.20 junho 2024
Cryptocurrency mining affects over 500 million people. And they have no idea it is happening.20 junho 2024 -
 How to Stop Websites from Mining Cryptocurrencies on Smartphone or PC20 junho 2024
How to Stop Websites from Mining Cryptocurrencies on Smartphone or PC20 junho 2024
você pode gostar
-
 Does Barbie or Oppenheimer have the higher Rotten Tomatoes score?20 junho 2024
Does Barbie or Oppenheimer have the higher Rotten Tomatoes score?20 junho 2024 -
 Petrosian vs Spassky, World Championship match 1966, Queen Sac20 junho 2024
Petrosian vs Spassky, World Championship match 1966, Queen Sac20 junho 2024 -
 Plan a Visit to Lassen Volcanic National Park20 junho 2024
Plan a Visit to Lassen Volcanic National Park20 junho 2024 -
 You are in charge of a live action Ben 10 movie what would you do20 junho 2024
You are in charge of a live action Ben 10 movie what would you do20 junho 2024 -
 Naruto Eyes Vector Art, Icons, and Graphics for Free Download20 junho 2024
Naruto Eyes Vector Art, Icons, and Graphics for Free Download20 junho 2024 -
 Lords of Chaos (2018)20 junho 2024
Lords of Chaos (2018)20 junho 2024 -
shamin pokemon go forma|TikTok Search20 junho 2024
-
 Russian Roulette Game for Android - Download20 junho 2024
Russian Roulette Game for Android - Download20 junho 2024 -
 Al Ittihad vs Sepahan: Predicted lineup, injury news, head-to-head20 junho 2024
Al Ittihad vs Sepahan: Predicted lineup, injury news, head-to-head20 junho 2024 -
Golden hamster - Wikipedia20 junho 2024